Table of Content
- Enabling UEM application blocking:
- Block and allow applications:
- Saved format and location:
- Blocked application:
- Log blocked application:
Security attacks in a managed desktop environment is always a threat. It is common within larger organizations to have a locked-down desktop environment to prevent accidental execution of malicious programs. On the 17th of March VMware released the new version of VMware User Environment Management (UEM). This blog post will take a closer look at the new UEM application blocking functionality.
Enabling UEM application blocking:
The new application blocking can be found in the the User Environment tab. 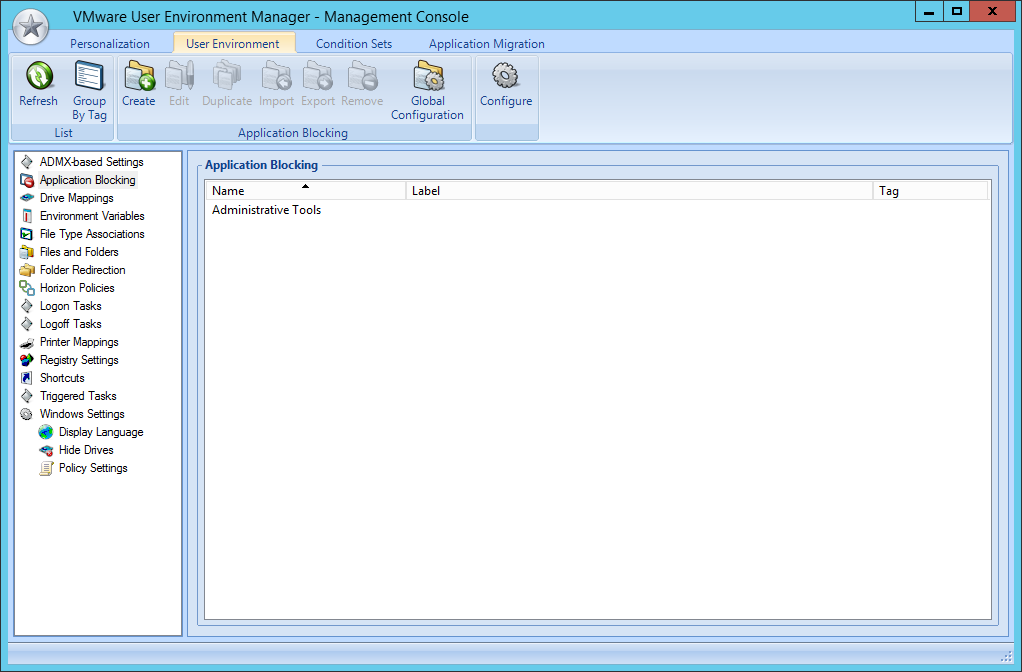
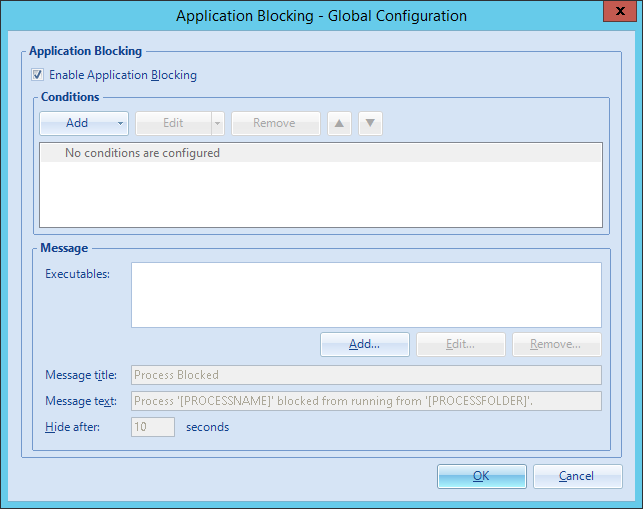
By default the application blocking is not enabled. In order to enable the functionality open the global configuration and check the checkbox.
Block and allow applications:
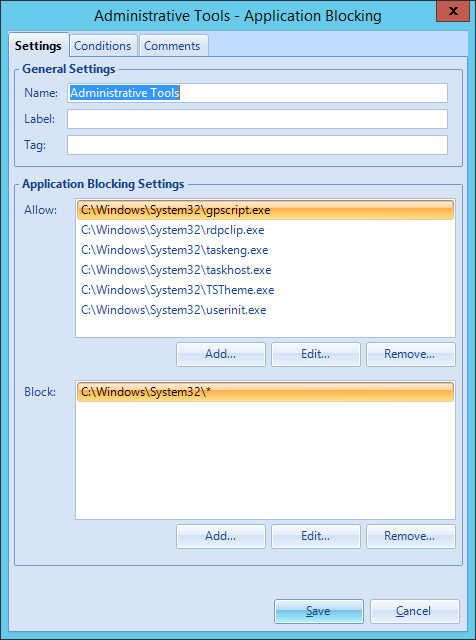
When creating a new application block setting there is the ability to allow and block applications. Here you can specify specific files or entire directories. When configuring a directory any program started from the location is blocked.
Please note: when blocking all application in the “C:\Windows\System32" directory the user cannot log on. Like shown in the screenshot multiple programs are required.
Saved format and location:
Just like any other setting in UEM a xml file is created within the share.
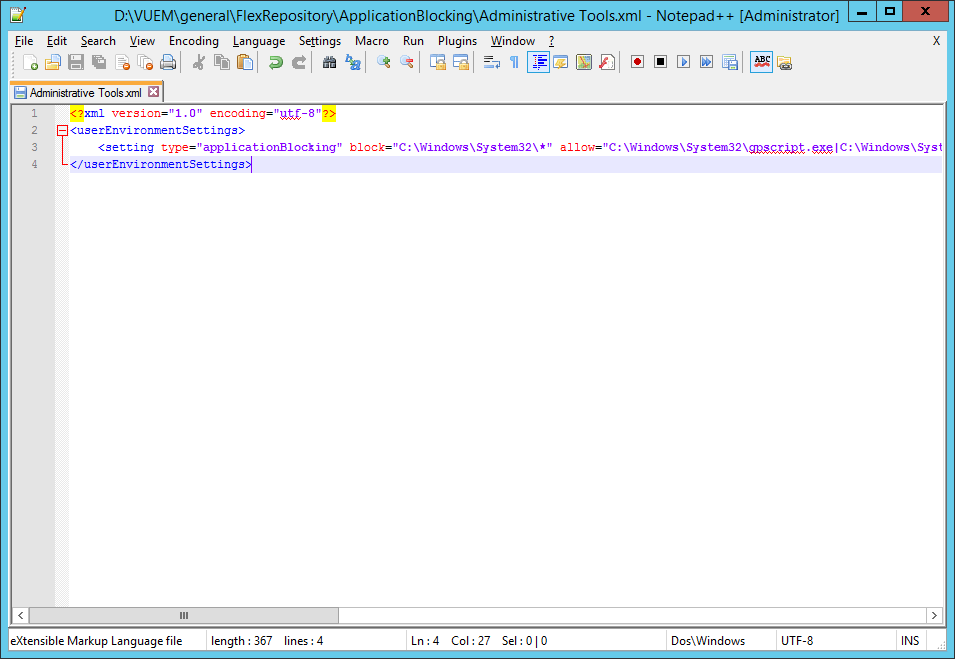
In the xml the setting is specified by “applicationBlocking”. Blocked applications are specified by “block” and allowed applications are specified by “allow” entry.
Blocked application:
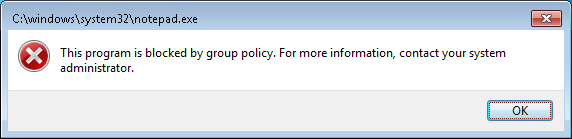
When an user is starting a blocked application he or she is informed by the following message.
Log blocked application:
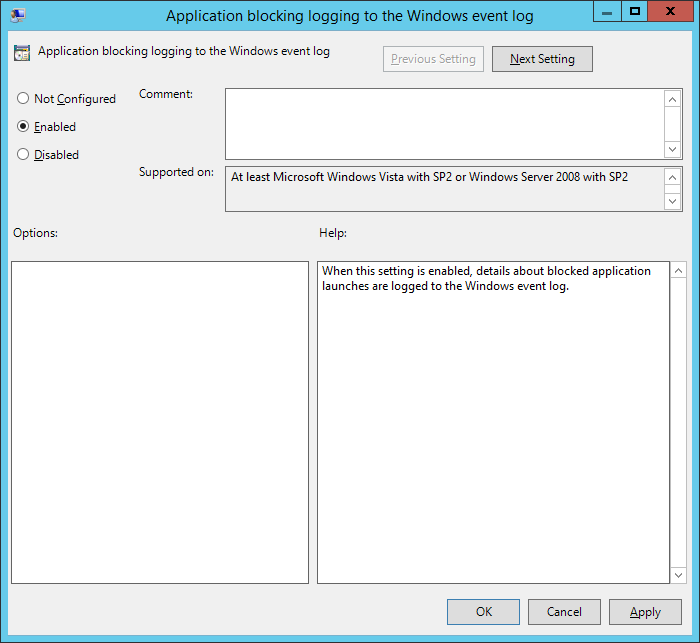
From a security point of view it is interesting to monitor the attempts to start a blocked application. Within the group policy objects of UEM logging can be enabled. When an attempt is done an entry will be created within the event log.
In my example I have blocked all the processes within the “C:\Windows\System32" directory. In that case it is useful to log attempts to start a blocked application. This helped me to understand which process are needed for an user logon.
Conclusion:
With this security feature, VMware UEM is becoming even more interesting for larger organisations. Security is nowadays very important within desktop environment by the all day threat of malicious programs. I hope this blog post is helpful and if you have question please leave a comment.